Phishing is basically when cybercriminals pretend to be someone you trust (like your bank, delivery service, or even your boss) to trick you into giving away sensitive information. It usually starts with a message that looks perfectly legitimate. Take this for example:
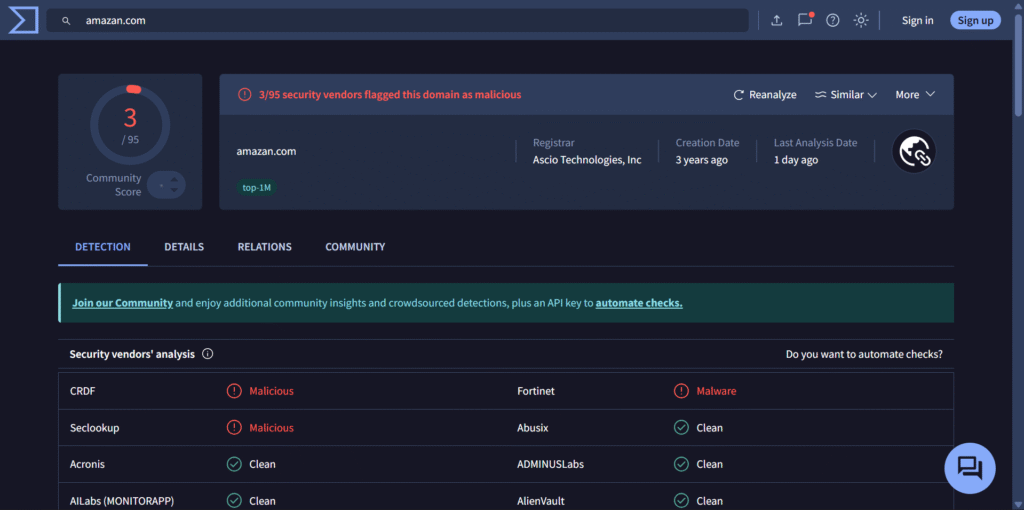
“Your package couldn’t be delivered. Click here to reschedule: https[:]//www[.]amazan[.]com”
Once you click that link or enter your login details, an attacker can steal your data, or even infect your device with malware. It’s simple, sneaky, and scarily effective.
What makes phishing so dangerous is how believable it’s become. Scammers do their homework. They’ll mimic official branding, use familiar names, and even time their messages to catch you off guard. They don’t need to hack a system, they just need to hack you.
In this article, we’ll be taking a look at various types of phishing, and what you can do to defend yourself, and your organisation.
So without further ado, let’s jump in.
Note: By the way, that shown link earlier is actually malicious. We’ve defanged it for your safety but if you’re still curious, take a look at the VirusTotal results below. (Of course, you can always mess around and find out by going straight to the source 🙂).
Types of Phishing
Phishing isn’t a one-size-fits-all scam. Over the years, attackers have found clever ways to adapt their tactics to different platforms, audiences, and even personality types. Some go after thousands of people at once, while others zero in on a single target with precision. Here are a couple of them:
- Spear phishing 🎯
- Bulk phishing 📧
- Whaling 🐋
- Smishing 💬
- Vishing 📞
- Quishing 📱🌀
Let’s take a look at each of them.
Spear phishing
Spear phishing is when attackers tailor their messages specifically for you or your company. They gather information like your name, previous job roles, internal projects, or corporate hierarchy. This can be gathered from social media platforms like LinkedIn, Instagram, Twitter, or even public documents. The more information they have, the better.
Once that has been gathered and processed, they send you message or two. The attacker might impersonate someone you know, refer to an ongoing project, or use your jargon. Anything to make it feel real and reduce suspicion.
In 2016, Snapchat, a social media company, fell victim to a spear phishing attack. Fraudsters impersonated the CEO and convinced the HR department to hand over some payroll information, resulting in the leakage of over 700 personnel data. Another example is Levitas Capital, an Australian hedge fund, where in 2020, attackers tricked one of its co-founders into clicking a Zoom invite, which was actually malware. As a consequence, the company lost £6.6 million ($8.7 million) in fraudulent invoices. Unfortunately, the company was unable to recover, and was eventually shut down.
Bulk phishing
Bulk phishing is the more familiar version of phishing. This is where mass emails (or other messages) are sent to a large number of potential victims with generic content. These usually aren’t personalised. Instead, they use broad themes like “Your password is about to expire”, or “Package delivery problem”, or “Update your account info”. The idea is that even if only a small percentage fall for it, the volume makes it profitable enough.
One example involves 16shop, a subscription-based service that let anyone launch bulk phishing campaigns with minimal skill. The platform helped attackers send convincing emails that mimicked trusted brands, tricking users into surrendering personal and financial data. Its reach spanned 43 countries, with over 70,000 victims worldwide. The operation came to a halt when the site’s Indonesian operator and two associates were arrested during a joint operation by Interpol.
Whaling
Whaling is like spear phishing but aimed at people in top positions such as executives, C-suite personnel, board members, or other high-profile individuals. Because these people often have authority, access to funds, or sensitive information, the stakes are higher, and so is the profit. Attackers often impersonate another executive, use urgent requests, or mask the request as something internal and confidential. And because executives are usually busy, they might skip the usual verification steps.
In 2014, Scoular Company suffered a £12.7 million ($17.2 million) loss in a classic whaling attack. Cybercriminals crafted highly personalised emails spoofing the firm’s CEO and accounting partners, instructing a senior executive to transfer funds for a fake merger. The emails used realistic business language and timing to bypass suspicion. The money was then wired to a Shanghai bank account linked to Dadi Co. Ltd. The attackers even answered phone calls to confirm the details, making the deception complete.
Smishing
Smishing is phishing via text messages (SMS). The attacker sends messages pretending to be from a trusted source (bank, courier, delivery service, or government agency), trying to make the recipient act quickly. The message might include a malicious link, a request for personal or financial information, or instructions to click or call to avoid a “penalty”. Because people often trust texts more (or are more distracted when reading them), these can be very effective.
This September in New York, residents reported receiving “Inflation Refund” texts, typically during peak daytime hours between 10 a.m. and 4 p.m. Each message claimed users’ refund requests had been approved and urged them to provide bank details before September 29. The scheme impersonated the Department of Taxation and Finance, tricking victims into submitting sensitive information.
Vishing
Vishing is phishing over the phone (calls or voicemails). Attackers impersonate a trusted person or organisation like tech support or bank fraud personnel. They try to play on your trust, fear, or confusion. And because the interaction is live, they can dynamically respond, use voice tone or urgency, and adapt based on what you say, making it harder to spot. Sometimes they use spoofed caller IDs or even an AI voice.
A case in the U.K. involved Emma Watson (not the actress), a businesswoman who lost £100,000 because of a call that claimed to be from her bank’s fraud team. The caller informed her there were fraudulent charges on her account and convinced her to transfer some money. More recently, AI-powered vishing has featured in impersonation campaigns. For example, the US secretary of state, Marco Rubio, was impersonated using AI in both voice and text messages to foreign ministers and other officials.
Quishing
Quishing uses malicious QR codes. Instead of clicking a suspicious link in an email or message, you scan a QR code that could either take you to a fake/malicious site, trigger a download, or harvests login/payment credentials. QR codes are often trusted because people think scanning them is safe, plus many security filters don’t inspect QR images like they do clickable links. Attackers might stick fake QR codes over real ones on posters, menus, or payment signs. They could also send QR codes in emails, or embed them in documents.
In the U.K., a driver scanned a parking QR code and was tricked into installing an app that charged him 90p, then signed him up to a £39 annual subscription. He realised the scam when the larger charge hit his account the following day and no refunds were available. In a separate event, a local MP urged more reports to the authorities after she removed fake QR stickers from parking machines in the city.
How to defend your organisation
As cybercriminals refine their tactics, the lines between phishing, vishing, smishing, and quishing blur. Whether it’s a fake email to a CEO or a deceptive QR code on a parking meter, the goal is the same: steal data and exploit trust. The good news is that both individuals and organisations can fight back. These are five practical things to do for solid protection against such attacks:
- Security Awareness Training 🧠
- Multi-Factor Authentication (MFA) 🔒
- Email and Endpoint Filtering Tools 🧰
- Verification Protocols and Incident Reporting 📞
- Regular Updates and Secure Device Practices📱
Security Awareness Training
Regular cybersecurity awareness training helps employees and individuals recognise and report phishing attempts before damage occurs. Through simulated phishing exercises, people learn to identify suspicious links, fake sender addresses, and emotional manipulation tactics. Awareness turns your employees into a “human firewall”, a strong defence line against deceptive emails, texts, or voice scams. If you want to test your phishing sherlock abilities, check out this Phishing Quiz by Google.
Or better yet, contact us for a personalised phishing simulation for your organisation.
Multi-Factor Authentication (MFA)
Implementing MFA ensures that stolen credentials alone are not enough for cybercriminals to access sensitive systems. Even if a user unknowingly gives away their password during a phishing attempt, the attacker is blocked without the second factor, which could be a code or hardware token. It’s a low-cost, high-impact security measure.
Email and Endpoint Filtering Tools
Using secure email gateways and anti-phishing software helps filter out malicious emails, smishing links, and suspicious attachments. These tools detect known phishing signatures and new variants, reducing employee exposure to threats. Furthermore, automation here prevents human error from becoming costly.
Verification Protocols and Incident Reporting
Always verify unexpected requests for payments, credentials, or sensitive data through a secondary communication channel. Calling the supposed sender via a different medium or confirming through an official portal helps catch phishing and whaling scams in progress. Quick reporting allows IT teams to contain and investigate incidents early.
Regular Updates and Secure Device Practices
Cybercriminals often exploit unpatched systems or outdated applications. Keeping software and mobile devices up to date closes the gaps attackers exploit through fake apps, QR codes, or links. Regular updates patch vulnerabilities and ensure antivirus systems stay effective. A secure device is far harder for phishing and quishing attacks to compromise.
And with that, cyber ladies and gentlemen, we have come to the end of this article. Hope you enjoyed it, and if you want to learn more about cybersecurity and how we help keep you and your organisation secure, visit us at Sycom Solutions.
Cover Image Credit: Shukhrat Umarov




